
Restoring S3 backups using Veeam
My coworker Yuvaraj and I were over thinking this WAY to much. I finally figured out how to do a full restore on a clean Veeam installation right out of the box.
Steven Panovski
My coworker Yuvaraj and I were over thinking this WAY to much. I finally figured out how to do a full restore on a clean Veeam installation right out of the box.
Add your S3 repository
Home ==> Backup Infrastructure ==> External Repositories
Confirm you have a valid bucket name, access key, and master key.
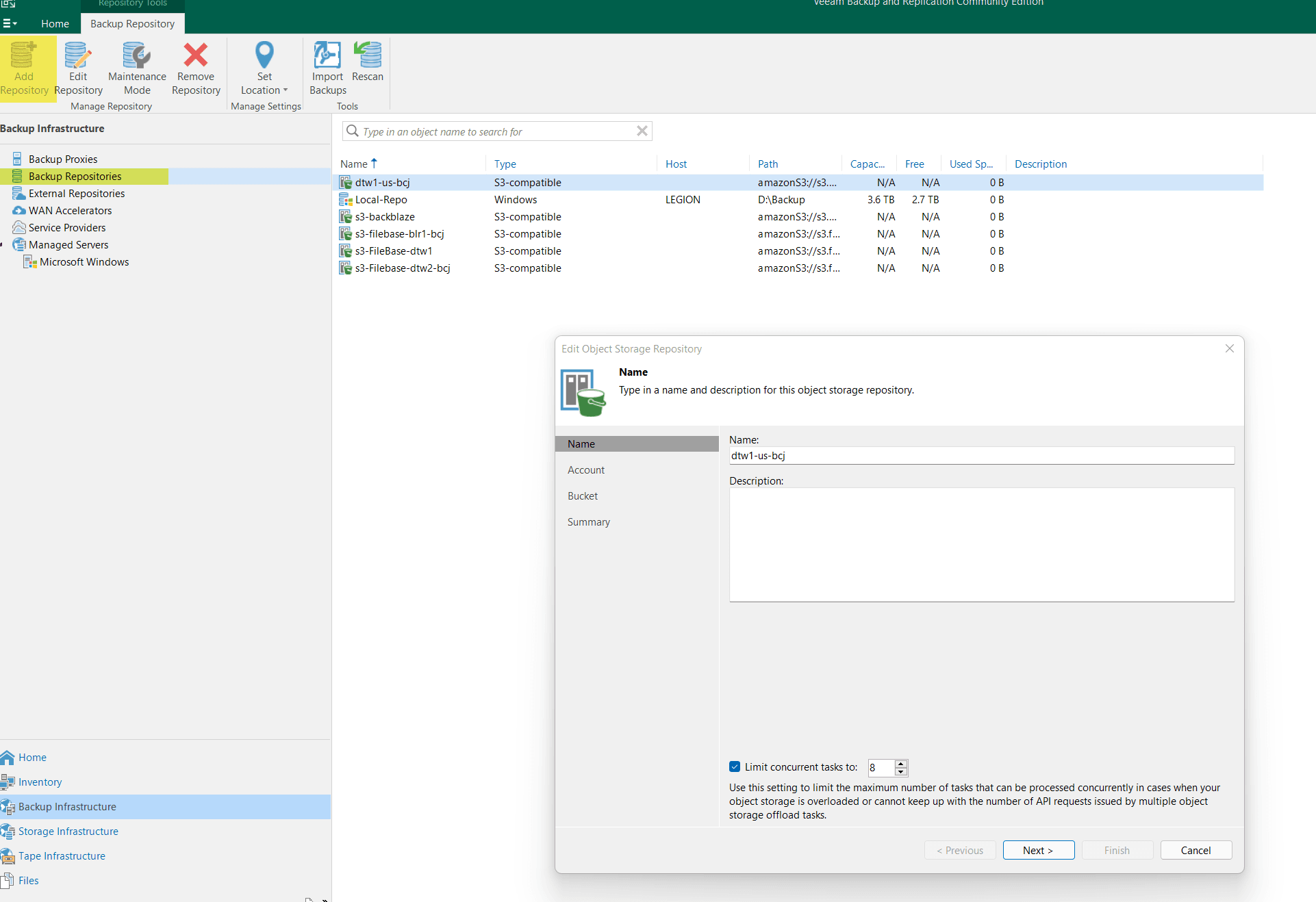
Import the backups from the S3 bucket into the Veeam
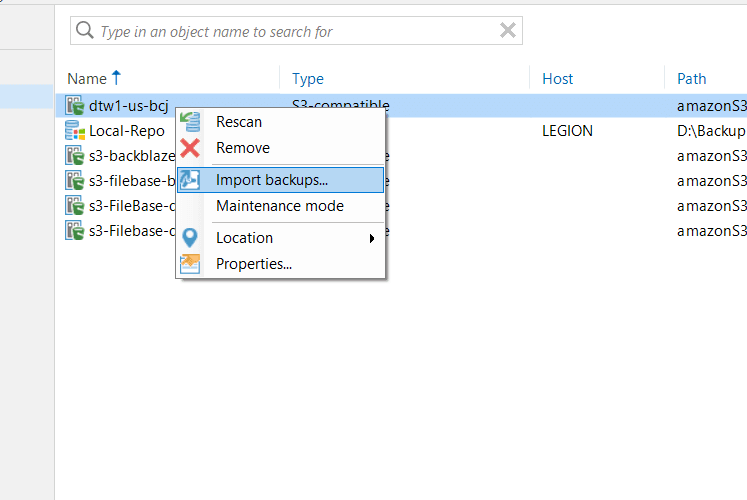
When the inventory scan of the S3 bucket is completed you will see the restore points in home menu.
Home ==> Backups ==> Object Storage (Imported)
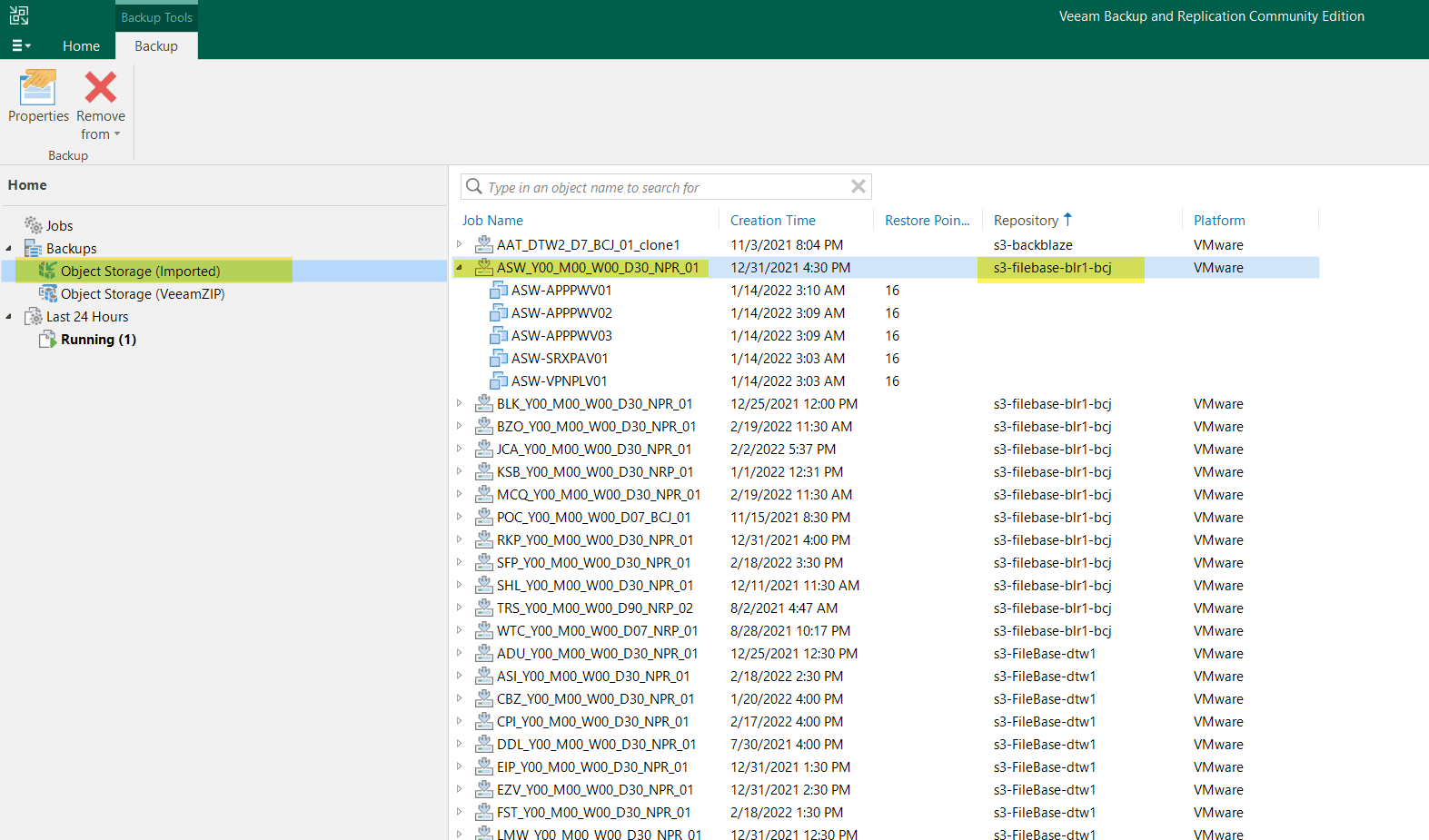
How a restore from an S3 object storage repository looks like

Related Posts
All posts

Another Microsoft Outage Proves the Value of UBX Cloud
Last week the world was reminded yet again of why Big Cloud needs to stay in its lane, and what happens when it doesn’t.

Team Member Profile: Hareesh Subramaniyam
Hareesh Subramaniyam joined UBX Cloud as a systems engineer straight out of college in 2021.
The Closed Loop: Why No One Does Managed Cloud Quite Like UBX Cloud
The approach UBX Cloud takes to managed cloud services, and why it works as well as it does.